The C919 is a relatively new narrow-body jet built by the Commercial Aircraft Corporation of China, or COMAC for short. It’s also apparently the beneficiary (and to some degree, the result) of massive hacking operations undertaken by the Chinese government and a government-affiliated hacking group, dubbed Turbine Panda.
A major report by the infosec security company Crowdstrike lays out the details, and it doesn’t mince words. The opening paragraph of the report states:
Short of kicking down the door just as a cyber actor pushes enter, it is frustratingly hard to prove who is responsible for cyber attacks with 100% certainty. However, a series of recent U.S. Department of Justice (DoJ) indictments released over the course of two years, combined with CrowdStrike Intelligence’s own research, has allowed for startling visibility into a facet of China’s shadowy intelligence apparatus.
The document describes a sustained effort by China’s Ministry of State Security (MSS) to create a network of cyber actors, MSS employees, and company insiders to steal key pieces of technology from the companies China hired to collaborate on the design of the C919. These operations, CrowdStrike says, can ultimately be traced to the MSS Jiansu Bureau. That’s the same group thought to be responsible for breaching the Office of Personal Management (OPM) back in 2015.
Designing the C919
It was already obvious a decade ago that China would one day be a huge market for air travel. The country knew that rising per-capita GDP would spark domestic interest in flying and it set out to build a low-cost narrowbody jet that would meet its own needs more effectively than a competing solution from Boeing or Airbus. The C919, while described as being years behind the latest jets from the Boeing / Airbus duopoly, also has a much lower flyaway cost. To meet its own plan for a jet, China allied with a variety of foreign companies to produce various components.
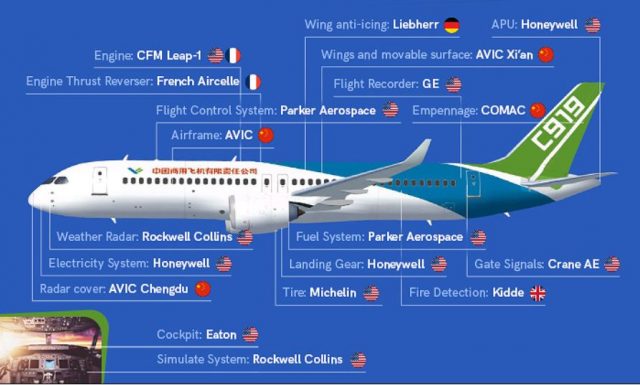
Image by Crowdstrike
In 2009, Comac announced it had chosen CFM International (a joint operation between GE Aviation and French aerospace firm Safran) to produce a variant of the LEAP-X engine, the LEAP-1C, for the C919. At the same time, Comac and another state-owned Chinese business, the Aviation Industry Corporation of China (Avic) were apparently tasked with designing a native Chinese design for the C919. In August 2016, Comac and Avic launched the Aero Engine Corporation of China (AECC), which produces an engine called the CJ-1000AX. The CJ-1000AX has long been suspected of being a copy of the LEAP-1C. The two engines share a great many suspicious similarities, including their dimensions and turbofan blade sizes. The first activity CrowdStrike observed in preparation for this theft came when Turbine Panda targeted the Los Angeles company Capstone Turbine in 2010, just a month after CFM was chosen as the engine provider.
Crowdstrike writes:
Though it is difficult to assess that the CJ-1000AX is a exact copy of the LEAP-X without direct access to technical engineering specifications, it is highly likely that its makers benefited significantly from the cyber espionage efforts of the MSS, which will be detailed further in subsequent blog installments, knocking several years (and potentially billions of dollars) off its development time.
We know so much about this specific situation because of indictments the Department of Justice has issued against various individuals, including “Sakula developer YU Pingan, JSSD Intelligence Officer XU Yanjun, GE Employee and insider ZHENG Xiaoqing, U.S. Army Reservist and assessor JI Chaoqun, and 10 JSSD-affiliated cyber operators in the ZHANG et. al. indictment.” The details revealed in these indictments have corroborated CrowdStrike’s own investigation.
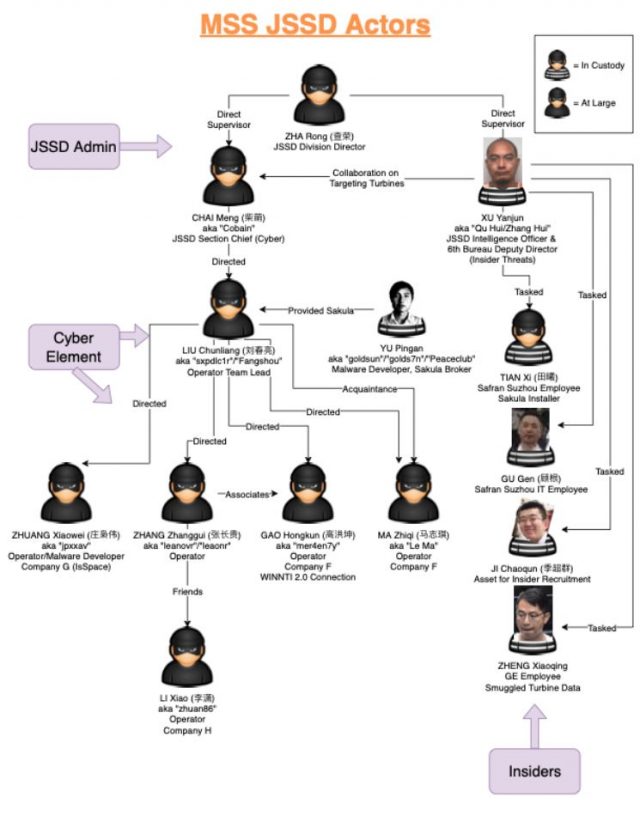
Image by Crowdstrike
Much of the rest of the report is a deep dive into the relationships between various individuals and the espionage they carried out. Honeywell and Safran were both targeted as well. Xu Yanjun recruited Zheng Xiaoqing as an insider informant and coached him on which technology to steal from GE. Ji Chaoqun entered the US on F-1 student visa to study electrical engineering in Chicago but agreed to work for Xu. He was, according to the report:
…eventually recruited to provide assessments on other high-value individuals in the aerospace industry for potential recruitment by the MSS. JI’s position in the U.S. Army Reserve program known as Military Accessions Vital to the National Interest (MAVNI) provided a perfect cover for JI’s assessment activities, as the program focuses on potential recruitment of foreign citizens with skills pertinent to national interest and legally residing in the U.S. Had it been successful, JI would have been handing XU other foreign-born recruitment candidates as they were about to enter U.S. military service on potentially sensitive projects.
The final section of the report is a discussion on what happened after these arrests and indictments were handed out. Despite the public nature of these indictments and events, China continues to mount attacks against US assets. The next-to-last paragraph of the report notes:
A major facet of the current Sino-U.S. trade war is forced technology transfer, which Beijing has used to great effect by siphoning intellectual property from foreign firms in exchange for providing joint ventures (JVs) and granting access to China’s lucrative market, only to be forced out later by domestic rivals as they grow competitive with state subsidies and support. Under current laws, the C919’s foreign suppliers (many of whom were targets of TURBINE PANDA operations) are required to physically assemble components in China through a JV with COMAC.
The original idea behind opening trade with China was that US and Chinese customers would both benefit. This has been true in many ways, but there’s a profound difference between manufacturing low-cost consumer goods and building high-performance aircraft parts with huge R&D costs. Such components are the end product of decades of research and manufacturing expertise. Far from competing on a level playing field, China appears to be focused on stealing the information it needs to close the gap with US companies, then limiting their access to its own market once it’s finished taking what it wants.
Now Read:

















